
What are the real cloud security challenges and dangers your business faces and what can you do to protect yourself?
“More than half (53%) of all businesses have migrated to the cloud, and 54% feel their security practices are immature and can’t keep up with the rapid expansion of cloud apps.” – Symantec’s Cloud Security Threat Report (CSTR)
Cloud Services Proliferation
The cloud has changed the way businesses operate today. It has become so deeply ingrained into everything we do, we sometimes forget that the cloud isn’t just a few services here and there, but a part of almost everything in a business and in your day-to-day life. Today, the cloud is the business. It is how businesses strive, and cloud security is critical to that.
While it has made everything easier, from collaborating with colleagues, to accessing new business opportunities around the globe – it comes with a serious set of cyber security challenges, including shining a light on the immaturity of internal IT security practices, the complexities of protecting a business from both internal and external agents, and the growing number of ways a business can be attacked. It amplifies the importance of partnering with knowledgeable cloud consultants to insure your company stays secure. When properly deployed, cloud computing is inherently more secure than on-premises environments.
Our dependence on traditional on-premises servers continues to diminish while Software-as-a-Service (SaaS) applications usage in the cloud is proliferating. Workloads are increasingly migrated from physical servers to cloud servers in the Microsoft Azure Cloud. This process has come in phases, as such, on-premises applications, storage, and private clouds persist. The result is a hybrid IT environment rife with challenges and existing security protocols aren’t up to standard to cope with these new complexities, leaving your IT staff scrambling to stay secure and keep up.
Set your IT team up for success by implementing a company wide security plan to minimize risk. Through this article, we will identify common challenges businesses face when adopting the cloud, and simple tactics and strategies to mitigate risk and protect your staff and assets, including Identity and Access Management, a Zero Trust strategy, and organizational policies for Cloud Governance. Understanding how threat vectors are shifting in cloud is fundamental to making the necessary updates to your security program and strategy. You can address cloud security threats with the right mix of technology, process, and an educated workforce.
The Reality of Cloud Security Challenges
In a recent study, Symantec surveyed 1,250 IT and operations security decision makers to understand the evolving cloud security industry, the extent of cloud usage, known or unknown, in a business and to gauge the maturity of security best practices in place as businesses transition some or all parts of their operations to the cloud.
The Symantec Cloud Security Threat Report found that businesses are often introducing cloud services without much forethought regarding how they will be used or their potential security risks, and this is creating a cascading series of problems for IT staff all the way up to Operations and Technology Officers. A frightening finding from the report shows 93% of respondents have issues tracking and managing all their cloud workloads. All it takes is one rogue application or improper procedure to open an issue. Left undetected, the potential for malware and data theft to run rampant skyrockets!
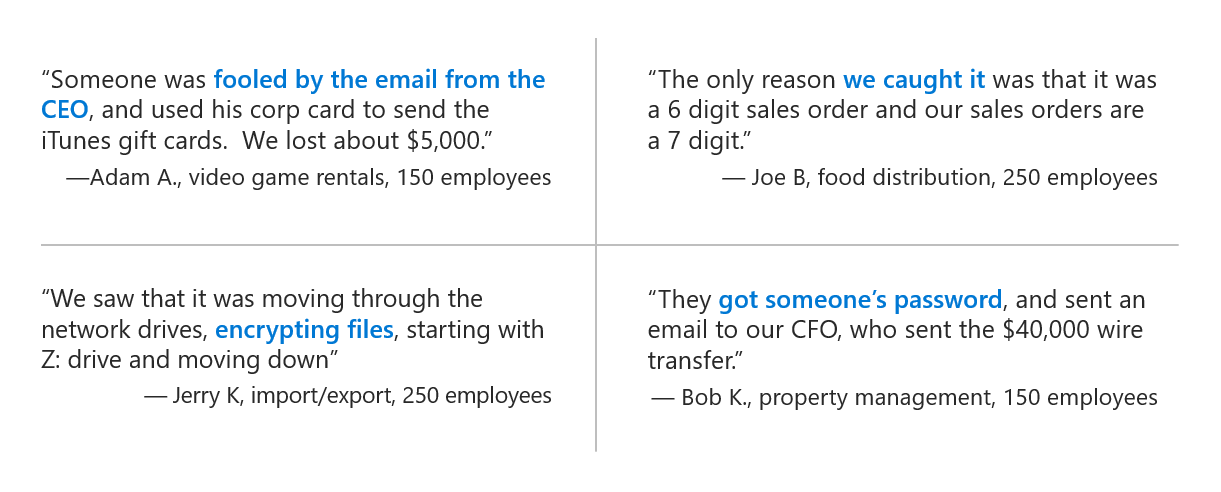
Underestimating the Depth and Breadth of Cloud Services in Today’s Business
It’s easy to download an app and start using it. We do this every day on our phones and computers without a second thought. We even do this on our work computers, but we need to stop and give it a second thought. The number of different cloud services and ease in which employees can download, install, and start using apps without your IT team’s knowledge or consent is staggering, and should be alarming for businesses. An app can easily request too many permissions, be malicious and contain malware and other executables, or share and capture personal and business information. Without proper security protocols to handle the proliferation of cloud services, it’s easy to lose track and expose your business to security threats.
Most IT departments are unaware of how many cloud apps are in use inside their organization and severely underestimate its use and growth rate. According to Symantec’s survey, “the average organization believes its employees are using 452 cloud apps. However, according to Symantec’s own data, the actual number of shadow IT apps in use per organization is nearly four times higher with 1807 cloud apps in use.” Cloud app deployment continues to grow at a rapid pace, increasing 16% over the past 12 months and expected to surge 22% in the next year. Underestimating the significant growth and usage of apps in your business, coupled with inadequate cloud security policies, organizations are facing a challenge to secure their cloud migration.
Quick Tip #1: Stay on top of these risks by having your usage monitored and know exactly what your company is using.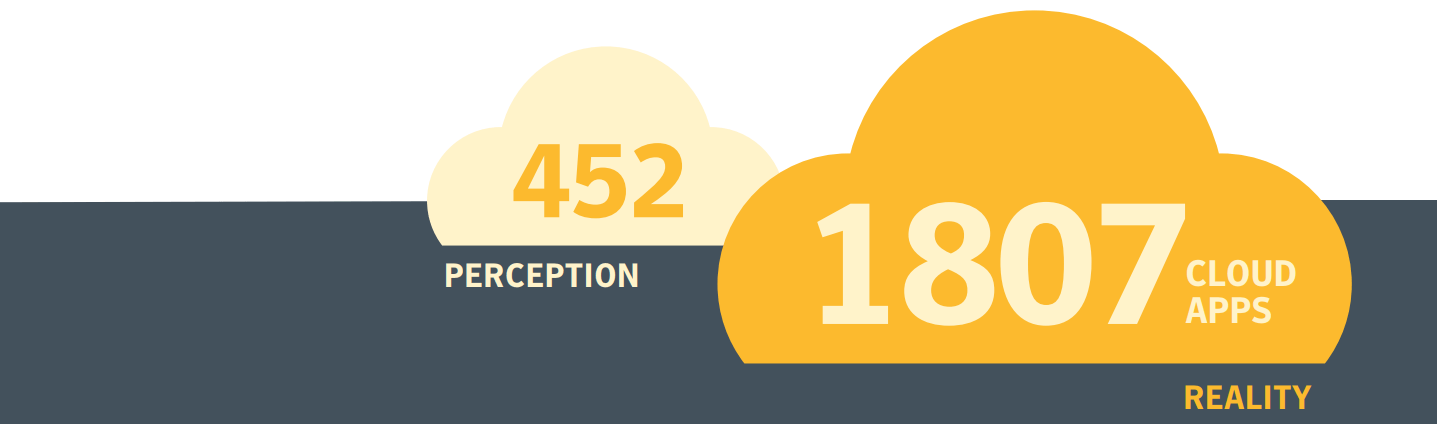
Cloud Security Threats Go Beyond Cloud Apps
We’ve discussed the potential security issues posed by unfettered organizational use of cloud apps, but they are not the only cloud data security threat you will face. The cloud, when configured and used correctly with the right security best practices can support and grow a business but implemented incorrectly could mean putting your organization at risk. One area to pay attention too is the cloud making it easier for you to lose control of your data. This happens in part due to poor cloud security controls and training. Oversharing cloud files containing sensitive and compliance-related data was cited as a problem by 93% of respondents in Symantec’s Cloud Security Threat Report study.
Quick Tip #2: Prevent this with proper staff training and standardized security practices.With how quickly cloud app and cloud service usage is increasing across businesses, many companies are finding themselves unable to adapt their security policies. 54% of businesses say their cloud security has not been able to keep up with the expansion of their use of cloud apps and services.
Quick Tip #3: Plan ahead and scale appropriately with security measures in place for a smooth transition.As a result of immature cloud security best practices and experience, organizations often underestimate the scale and complexity of cloud attacks as well as their true impact on operations immediately and over time. Cloud attacks can irreparably damage a business’ livelihood and reputation. The most commonly investigated cloud security incidents identified in the survey were Distributed Denial-of-Service DDoS attacks and cloud malware injections. Stopping a data breach is difficult without the correct procedures in place to detect it but could also be prevented if those policies were practiced. Unauthorized access threats account for 64% of data breach incidents.
Small businesses are vulnerable to cyberthreats

Some cloud security threats are unexpected and can pose the greatest risk from those within the company. Accidental insider threats from those who are closest to the organization (trusted insiders with access to protected data) represent some of the greatest risks. Once data has been exposed, a new threat rises. That is the sale of your compromised data on the Dark Web. 68% have seen their data for sale, however, only 31% believed their data was at any risk.
These numbers clearly show that organizations are struggling to keep pace with the shift to the cloud as their internal security rules and procedures are inadequate. Symantec data shows that 85% of companies are not using the best cloud security practices as outline by the Center for Internet Security.

How to Fix It
Instead of applying more manual effort into finding Shadow Data and IT, organizations should enlist advanced automation and analytics services to help identify and prioritize risky behaviors, identify malicious users, and escalate crucial security alerts.
Suggested Tools: Microsoft 365 Business
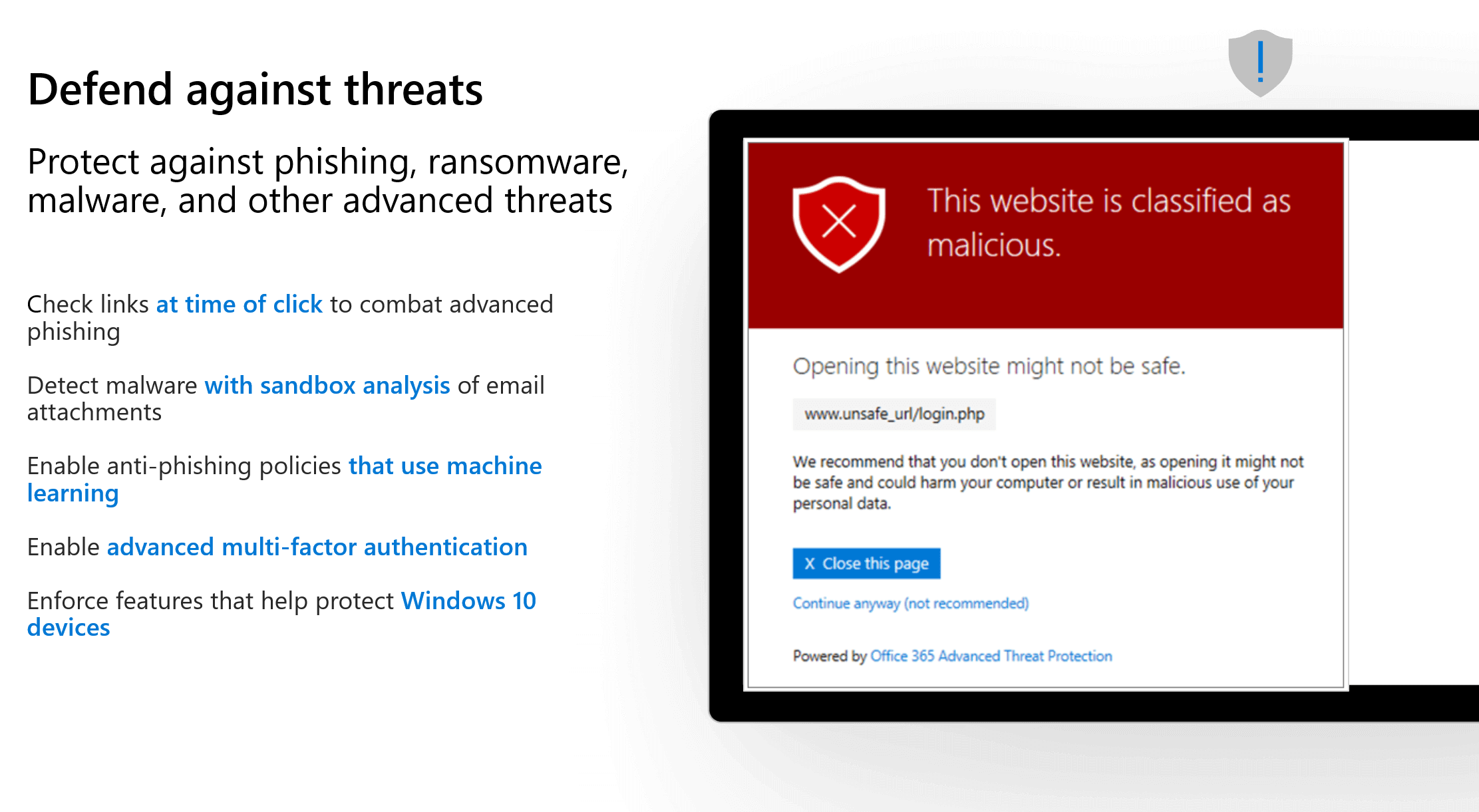
All the capabilities of Office 365 Business Premium, plus advanced cybersecurity, data protection, and device management to quickly implement a cloud-based security solution that stays current and protects you from the latest threats in phishing, ransomware, and malware.
Internal Cloud Security Threats as Harmful as External Threats
One of the biggest challenges for IT security teams when implementing a Cloud Security Strategy is risky user behavior. Nearly 1 in 3 employees engage in risky behavior on the cloud, and Symantec’s own data shows that 85% of businesses are not using cloud security best practices.
With higher incidents of insider threats, immature security best practices are hindering businesses. 65% neglect to implement Multi-Factor Authentication (MFA) as part of their cloud app and cloud service configuration. 80% don’t use any kind of encryption.
The most common symptom of lax cloud security is poor password hygiene. On average, 37% of users will use weak and easy to break passwords, and 34% are not protecting their passwords or changing them regularly. Essentially, employees are forgetting to lock the door behind them and letting strangers into your business.

How to Fix It
With employees accessing websites from anywhere and BYOD bringing massive amounts of devices into the enterprise ecosystem, it’s critical to implement total endpoint security to protect devices, apps and networks against malware, ransomware and other emerging threats.
Suggested Tools: Microsoft 365 Business
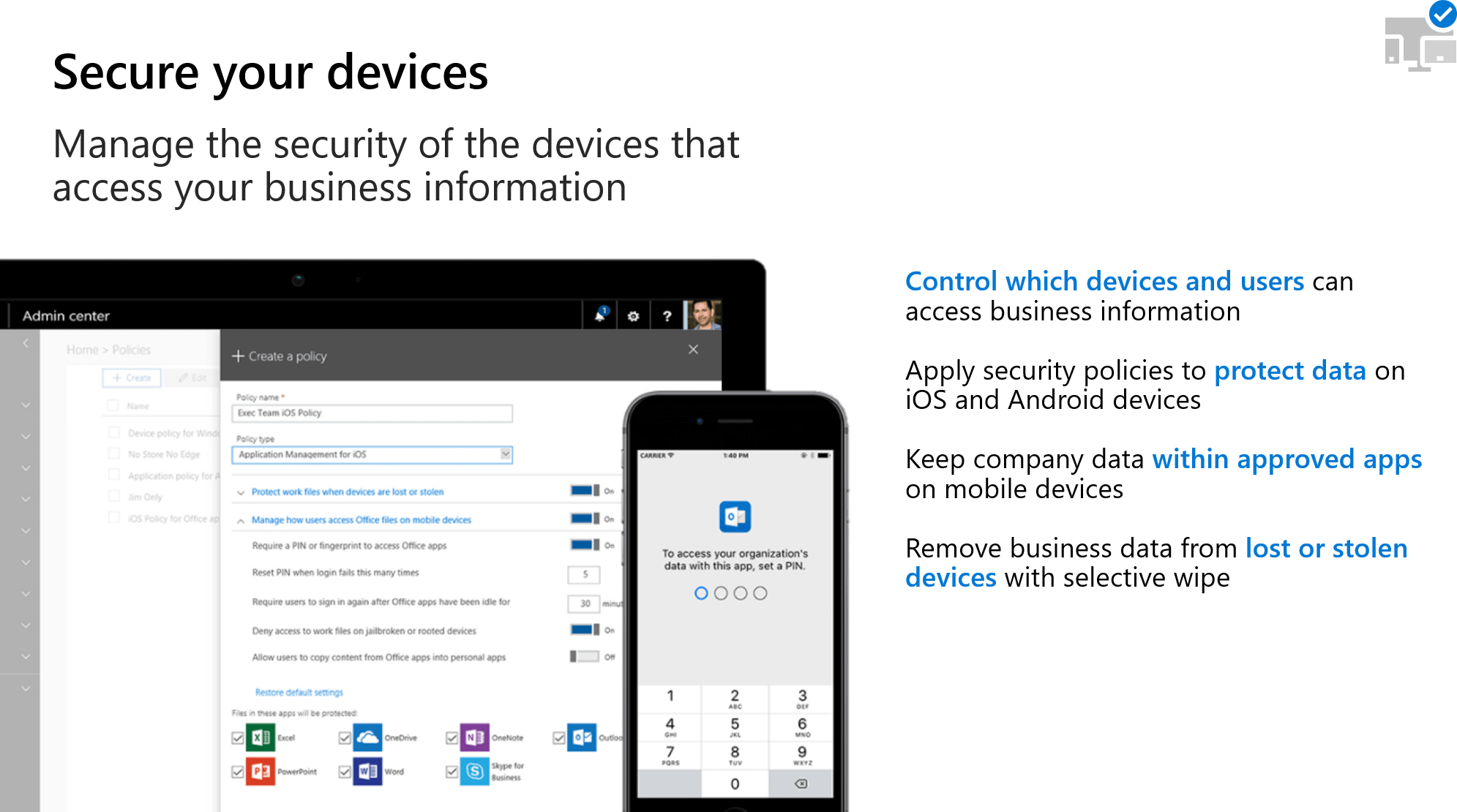
Microsoft 365 Business helps you manage the security on all the devices that access your data – phone, tablets, PCs, macs. …whether they are Windows, iOS, macOS, or Android, Microsoft 365 Business helps you manage them.
Implementing Cloud Security Best Practices to Protect Your Business
More than half of respondents in the external survey confirmed their cloud security practices were not mature enough to meet the demands of the growing use of cloud apps, and nearly three-quarters said they experienced a security incident in cloud-based infrastructure due to this immaturity.
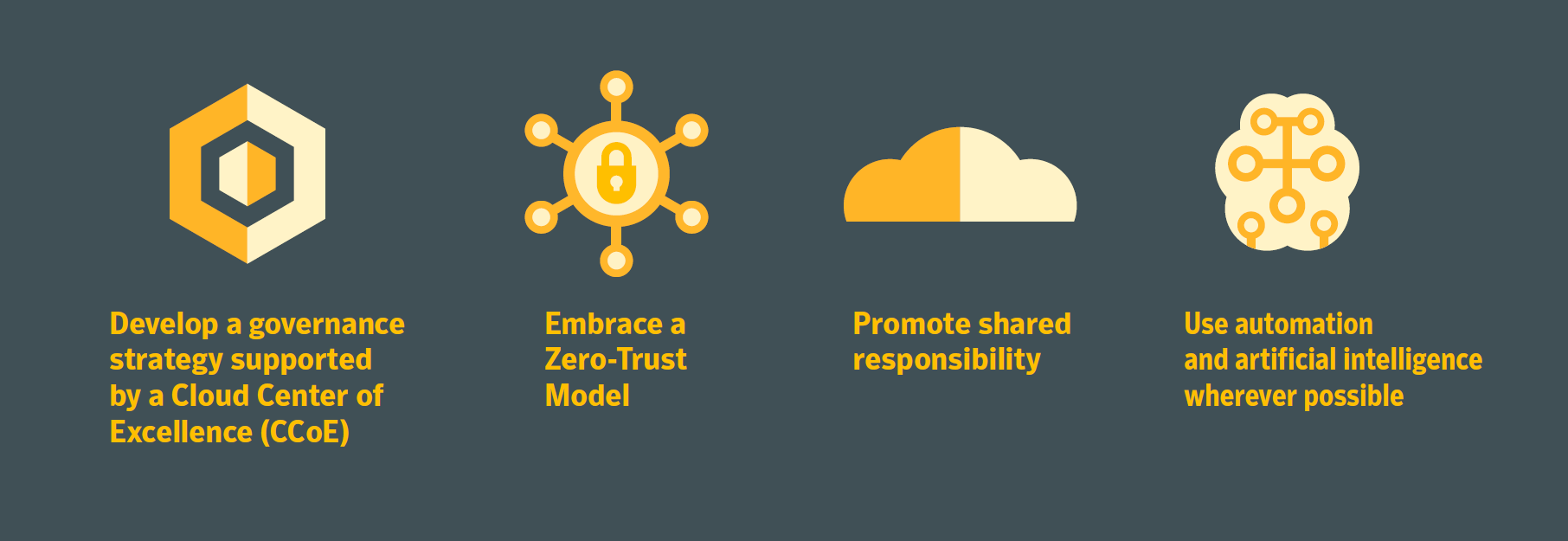
Companies that continue to engage or accelerate cloud services without a plan to mature their security practices do so at their own peril. Organizations should consider these key steps to shore up their cloud security posture:
Develop a Governance Strategy Supported by Cloud Best Practices
Any change to business processes or technology platforms introduces risk to the business. Cloud Governance teams, whose members are sometimes known as cloud custodians, are tasked with mitigating these risks with minimal interruption to adoption or innovation efforts.
However, cloud governance requires more than technical implementation. Subtle changes in the corporate narrative or corporate policies can affect adoption efforts significantly. Before implementation, it’s important to look beyond IT while defining corporate policy.
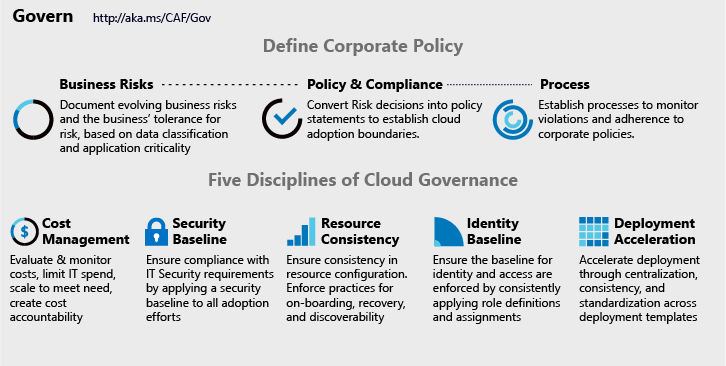
Define Corporate Policy
Businesses can identify and mitigate risk regardless of the cloud platform they operate on by defining corporate policy. A healthy cloud governance strategy begins with a properly defined corporate policy with acceptance from all levels of the organization. Using the three-step process can help guide you to develop these policies.
- Business Risk
Identify any current cloud adoption or migration plans and analyze potential risks to the business. Work with operational departments to balance risk tolerance and potential costs. - Policy and Compliance
Evaluate organizational risk tolerance levels to develop the least invasive policies for cloud adoption. Manage risks as some industries have third-party compliance that affects your initial policy creation. - Processes
The rapid pace of cloud adoption and innovation will naturally result in violations. Having relevant processes and identifying risks will help to monitor and enforce policies.
Disciplines of Cloud Governance
There are common cloud governance disciplines that can serve as a guide to help inform your corporate policies when deploying infrastructure and services in the Microsoft Azure Cloud. Using these disciplines, you can guide decisions regarding the proper level of automation to employ and how to enforce corporate cloud policy.
- Cost Management
Growing costs can be a major concern when adopting cloud technologies. Develop policies to balance performance demands and adoption pacing. - Security Baseline
Establish initial security requirements and develop cloud governance policies to enforce security parameters across networks, data, and software. - Identity Baseline
Applying a consistent framework for identity management across cloud services can mitigate the risk of breaches. Develop a governance strategy that prioritizes identity services as its primary security parameter. - Resource Consistency
Cloud operations success can be improved through resource consistency. Resources can be consistently configured to mitigate risks, reduce on-boarding time, and accelerate recovery. - Deployment Acceleration
Centralization of cloud services, standardization’s, and consistency in deployment and configuration improve cloud governance practices.
Embrace a Zero-Trust Model
A Zero-Trust model is based on the principle of maintaining strict access controls and not trusting anyone by default. This includes those already inside your network like employees. By instilling a Zero-Trust security model, you are taking a holistic approach to your network security that prevents attackers that gain access to your network to have free reign on everything inside.
Principles and Technologies Behind Zero-Trust Security
The core philosophy of a zero trust network states that to truly develop the ability to defend your network, you must assume that attackers are both within and outside of the network, so no users or machines are trusted by default.
Traditional IT network security entrusted the concept of the castle and moat. In castle and moat security, it was hard to obtain access from outside the network due to many layers of external defense like firewalls. Everyone already in the castle is trusted automatically. The problem arises when an attacker does breach the defense and is inside the castle. The attacker is now trusted and free to do anything. In zero trust network security, no one is trusted by default, whether inside or outside. This added layer of security has been shown to prevent data breaches.
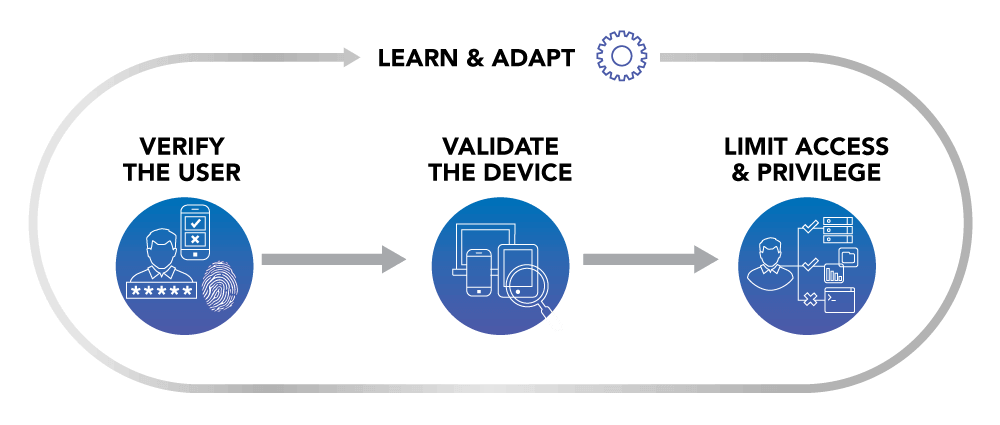
Multi-Factor Authentication (MFA)
Multi-factor Authentication (MFA) is a critical component of zero trust security. MFA functions by requiring more than one piece of identification to authenticate a user. A password alone is not enough to prove your identity and gain access as passwords can be compromised. Using MFA to deploy 2-factor authentication is a common solution used by companies like Google and Facebook. A user would enter a password and must also enter a code sent to another device, usually a mobile phone, to provide two pieces of identification to verify who they claim to be.
Azure Active Directory (Azure AD)
Controlling user access and permissions is another critical component to zero trust security. By segmenting areas of access and limiting functionality to only the essentials needed for that user profile prevents unauthorized access after a user has logged in. To facilitate this, businesses can leverage Azure Active Directory (Azure AD) in the Microsoft Azure Cloud platform.
Azure AD provides robust, adaptive, standards-based identity verification, including automatic protection against many attacks. It also allows admins to express their access requirements in simple terms. Virtually every aspect of each sign-in (including associated user or session risk) is available to define the conditions under which access policies are applied. A framework of controls such as additional authentication factors, terms of use, limited access, and other session semantics regulates access. This guarantees we are “secure at access” in our Zero Trust approach.
Promote Shared Cloud Security Responsibility
Cloud platform providers take their security infrastructure and compliance responsibilities very seriously. The cloud continues to be a secure and robust infrastructure that can be more secure than on-premises deployments.
Cloud providers, like Microsoft Azure, have made it clear that their responsibility for security and compliance can only go so far. Customer must keep up security and governance on their end too. This shared cloud security responsibility model is widely adopted among most cloud platform providers in the market.
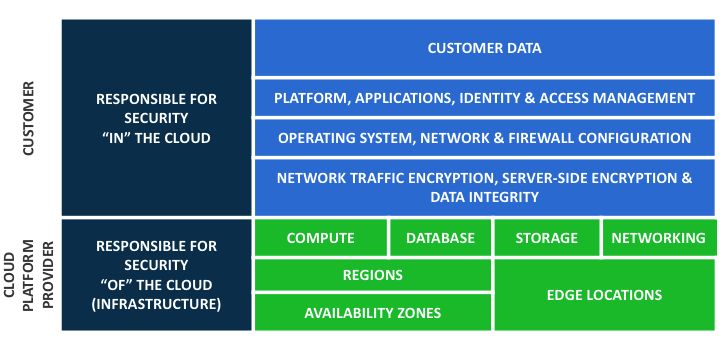
The cloud provider is responsible for security of the cloud and the customer is responsible for security in the cloud. According to a recent Gartner report, it is expected that over the next five years, at least 95% of cloud security failures will be the customer’s fault. Ensuring a proper cloud governance strategy that promotes shared responsibilities is essential to securing your cloud deployment. Don’t let your company add to this statistic.
Quick Tip #4: Be proactive in your security practices and partner with cloud experts.Use Automation and Artificial Intelligence Wherever Possible
Security can be a never-ending saga. Attacks become more frequent and intelligent – evolving to step around your efforts to thwart them. It has become difficult for cloud security teams to keep up the number of threats and sophistication. Implementing automation and artificial intelligence to rapidly identify, analyze, and eliminate threats without human intervention frees up your IT team to focus on their normal tasks.
Microsoft 365 Business gives you peace of mind by helping to safeguard your business. And it does this three ways:
- Get protection from sophisticated external cyber threats hidden in email attachments and links, and get cutting-edge defenses against phishing and spoofing attacks, ransomware, and other advanced malware attempts.
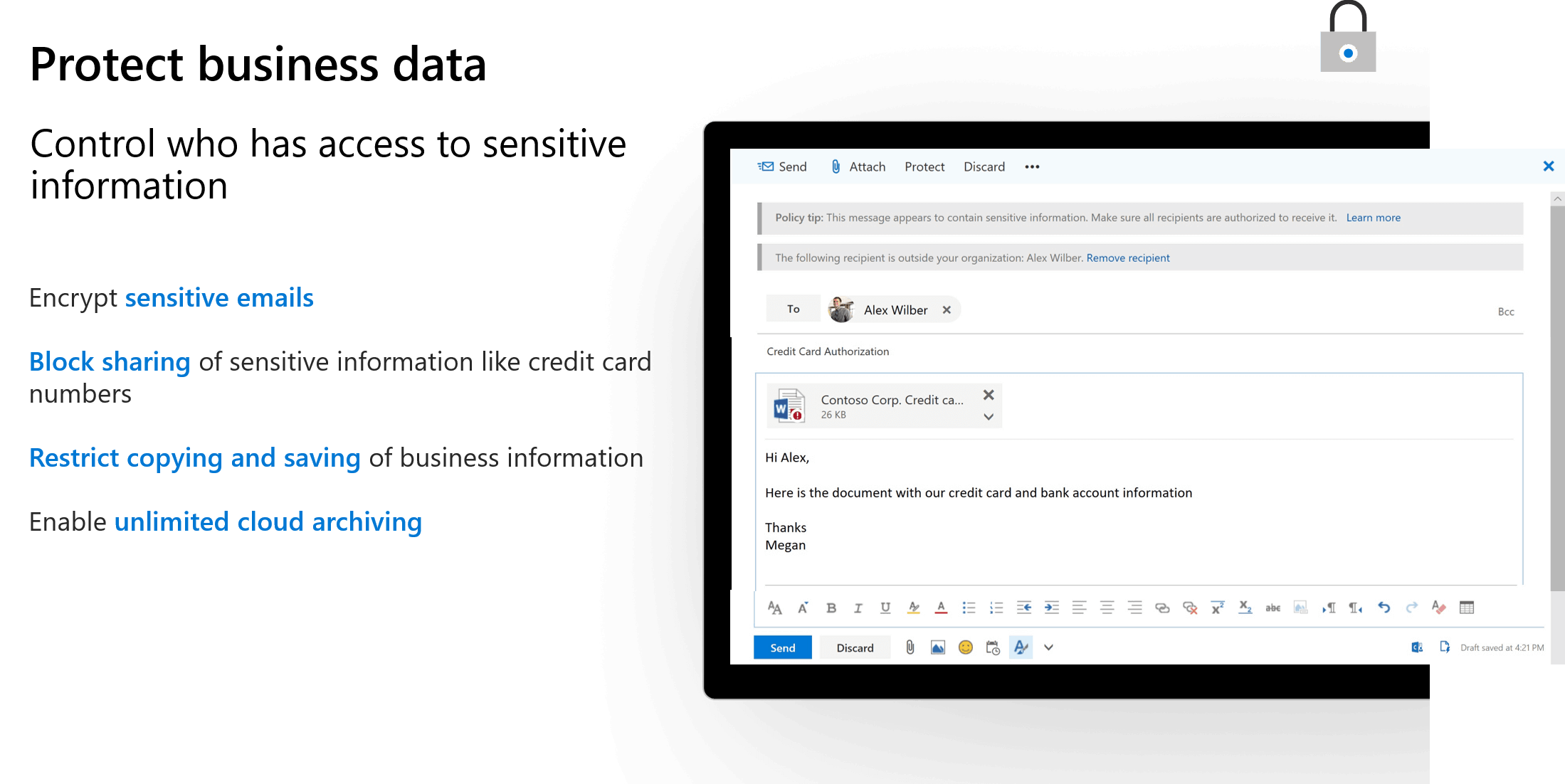
- Gain more control over your company data and documents. Protection from data leaks helping you prevent sensitive information like SSNs and customer credit card numbers from being shared outside your business, and control access to documents, even after those documents have been shared outside your company.
- Manage the apps, data, and documents on devices that access your company data. Regardless of the device type or operating system, iOS, macOS, android, or Windows. Microsoft 365 Business helps you manage these devices.
Get a Handle on Cloud Security
For an already overworked and understaffed IT team, adding cloud security responsibilities to your duties can be stressful. Managing and protecting assets and users requires tact, rapid response, and guidelines to streamline the process.
While moving applications, data and workloads to the cloud can improve efficiency for your organization; for IT infrastructure and network security teams, this creates a significant increase in work. The ability to instantly deploy servers with no capital costs is well received by businesses. However, there are hidden costs. Incorrectly configured and weak security settings can put your cloud infrastructure at risk. The cloud can be secure, but to have a chance, IT security teams need the proper knowledge, tested processes and a platform to deploy, manage, and secure each part of the infrastructure and its users.
Microsoft Azure Cloud platform, Microsoft 365 Business and the many built-in security automation tools are a starting point for adopting and deploying the cloud successfully. Three primary factors are necessary for your IT security team to have success protecting your business: Visibility into your assets in the cloud, integration with a variety of information sources on threats, and the automation necessary to apply policy and respond rapidly.
Visibility into your Cloud Infrastructure
The Microsoft Azure Cloud has simplified the process of provisioning cloud services and infrastructure resources for different business departments. However, with new servers and services being turned on and off just as quickly, it has become much more difficult to truly see what assets your business has in the cloud.
While it is common for shadow IT, i.e., unsanctioned services and infrastructure deployed without proper approvals or documentation, to pop up inside your office, these are causing headaches for cloud security teams.
Gaining visibility into what services and infrastructure have been deployed, by whom, and what data is in the cloud is necessary in order to see clearly and act faster before security threats occur.
Information All in One Place
Leveraging a connected platform for cloud services and apps has the added benefit of placing the vital information on the security state of all endpoints, servers, apps, and cloud infrastructure into a single dashboard. To get the best visibility into the health of your company’s security, that information needs to be consolidated and readily accessible in a single view.
The Microsoft Azure Cloud Portal is a central dashboard to view, manage, and maintain all provisioned cloud infrastructure services, and gain visibility into the services and apps running in the cloud. Fundamental to the Azure Cloud Portal is security, with advanced threat analysis and protection protocols in place.
Having everything in one place is essential but knowing how to use this data and manage it is a challenge. The Cloud Security experts at 360 Visibility have the advanced situational awareness and experience to effectively manage your cloud infrastructure, services, apps and overall security so your IT can stay focused on internal tasks. Staying on top of the evolving nature of cloud security is another challenge that can be overcome by shifting cloud infrastructure management to 360 Visibility.
Cloud Security Automation for Apps and Cloud Services
Most companies do not have enough IT security staff or resources, let alone qualified security experts that are up to speed on the ever-changing cloud security landscape. By introducing automation into the mix, the process of detecting threats, deciphering positive and false-positives, and enforcing policies can help companies respond rapidly to incidents. Threat detection and mitigation are key areas for increased cloud security automation.
To give security teams better visibility into threats to their company’s cloud deployments, Microsoft has integrated the following tools in the Azure Cloud Platform:

Azure Security Center

Azure Key Vault

DDoS Protection

Azure Information Protection

Azure Application Gateway
Click here to see all Azure Cloud Platform Tools and Services
Implementing and Managing Cloud Security Governance and Automation
The connected and online nature of modern business environments has added a broader set of vulnerabilities and threat potential. Huge gaps in visibility, security best practices, and IT resources leave organizations in the dark about how much and where data resides, making it harder to identify and mitigate cloud security risks.
Too many companies are underestimating the impact of potential cloud security threats and overestimating their ability to mitigate and withstand attacks with their current levels of IT and cloud security resources. Investment into cloud cyber security platforms – like Microsoft 365 Business– that leverage automation and AI to supplement human resources is a clear way to automate defenses and harden your business from malicious agents internally and externally.
Related Post: Microsoft Office 365 E3 vs Microsoft 365 Business
Microsoft 365 Business
Working with a Microsoft Cloud Solution Provider that understands cloud cyber security and your business is critical to deploying and managing a cloud security governance policy that is respected and adhered organization-wide along with a system to automate threat protection.
360 Visibility’s Cloud Cyber Security team is at the forefront of deploying and integrating Microsoft’s advanced threat protection and security protocols for your company’s data, staff, and workloads, and understand the critical elements to work with you to develop cloud security policies to safeguard your operations.
Contact 360 Visibility to speak with our Cloud Cyber Security team. We will work with you so that your technology and staff adopt security best practices, ensuring your business is protected from potential cloud security threats.



